
On this series of articles we are going to talk about how we can improve the security of our tenant.
Firstly we are going to talk about how to avoid Enterprise Applications Phishing Attacks.
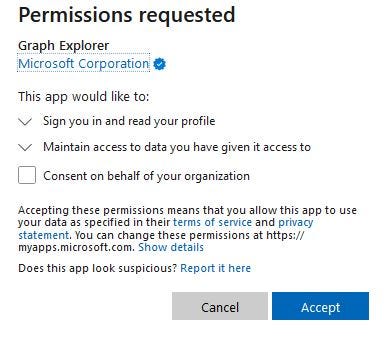
Enterprise Applications allow integration of first- or third-party apps with Microsoft 365, providing access to data like Single Sign-On, files, and emails. However, attackers exploit this by tricking users into adding malicious Enterprise Applications to a tenant, granting the app permissions that bypass Multi-Factor Authentication (MFA) and password changes. This method can also be used to launch ransomware attacks on Exchange Online.
To disable the ability for users to grant consent for Enterprise Applications, open the Azure AD admin center, navigate to Enterprise Applications > Consent and Permissions
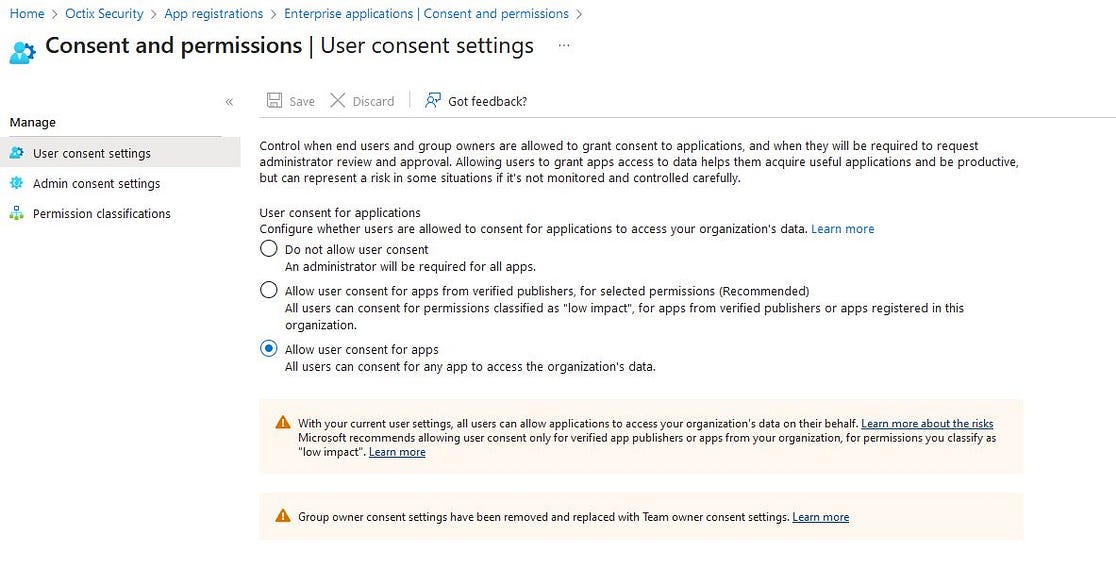
We will se that we have by default the option Allow user consent for apps applied. Now we have to choose either Do not allow user consent, or Allow user consent for apps from verified publishers, for selected permissions. I recommend the first option as this gives you total control of Enterprise Applications within your organization.
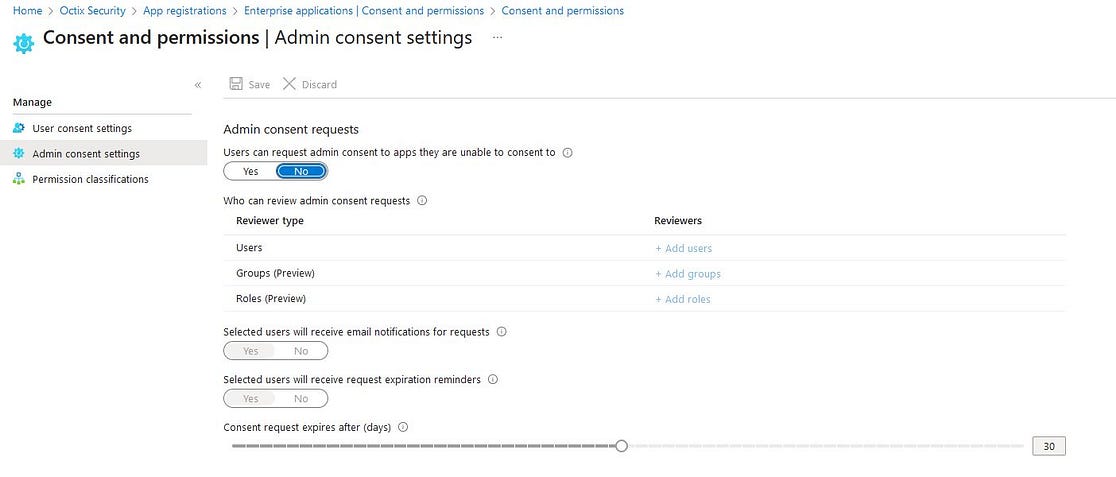
If you choose the first option, I recommend enabling the Admin consent workflow. This allows users to request reviews and approvals for applications. You can also specify which users are authorized to approve the applications.