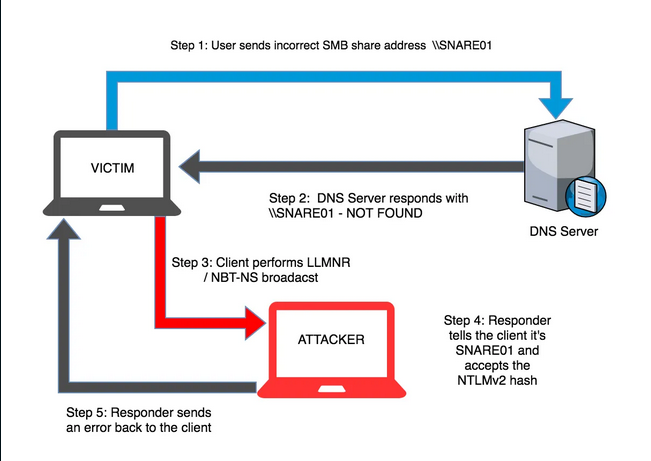
What are they?
NetBIOS over TCP/IP and LLMNR are broadcast protocols primarily used for compatibility with older Windows systems. However, both are vulnerable to spoofing and MITM attacks. Tools like Metasploit offer pre-built modules that exploit vulnerabilities in these protocols to intercept user credentials on local networks, including NTLMv2 hashes. To enhance your network security, it’s essential to disable these protocols within your domain network. This guide explains how to disable LLMNR and NetBIOS protocols in Windows 10 and Windows Server 2019, either manually or via Group Policies.
NetBIOS and LLMNR protocols allow computers on the local network to find each other if the DNS server is unavailable. Perhaps they are needed in a workgroup environment, but in a domain network, both of these protocols can be disabled.
How to disable LLMNR in Windows?
In the domain environment, LLMNR broadcasts can be disabled on computers and servers using Group Policy. To do it:
- Open the
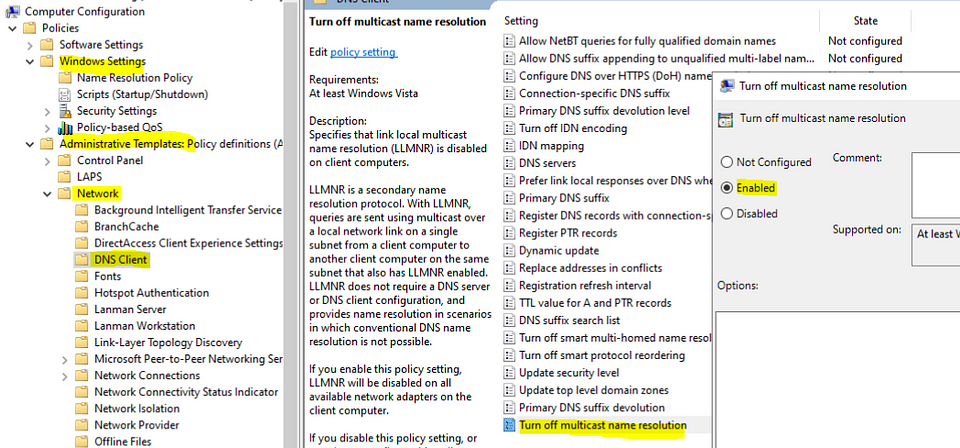
gpmc.msc, create a new GPO or edit an existing one that is applied to all workstations and servers; - Go to Computer Configuration -> Administrative Templates -> Network -> DNS Client;
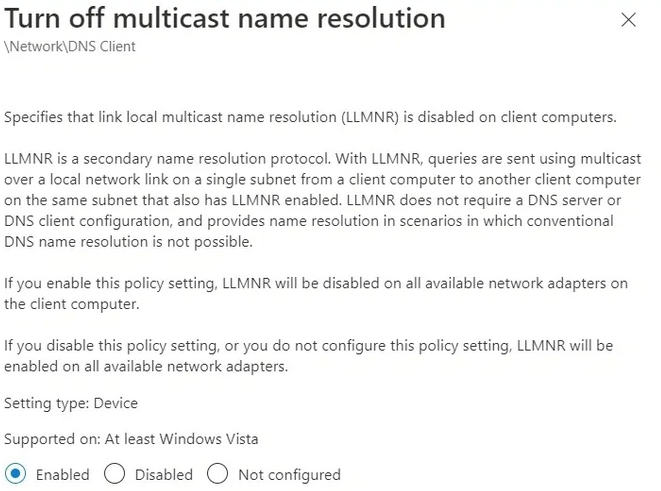
- Enable Turn off multicast name resolution policy by changing its value to Enabled;
How to disable LLMNR in Intune?
Disable LLMNR Protocol for all network adapters. You should be able to disable LLMNR Protocol from Intune — Windows — Configuration Profile — Administrative Templates — Turn off multicast name resolution.
How to Disable NetBIOS Over TCP/IP via Group Policy in Windows?
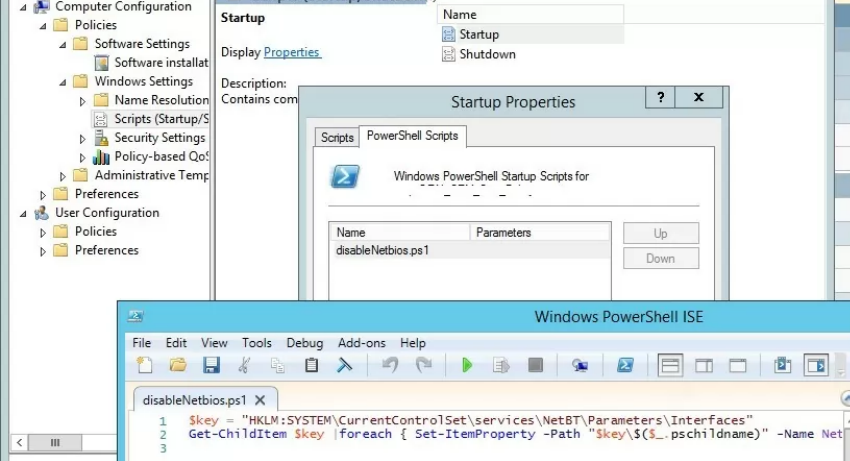
There is no separate GPO option that allows disabling NetBIOS over TCP/IP for all network adapters in Group Policy Editor or the latest version of Administrative Templates for Windows 10/Windows Server 2019. Use the following PowerShell logon script to completely disable NetBIOS for all network adapters:
$regkey = "HKLM:SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces"
Get-ChildItem $regkey |foreach { Set-ItemProperty -Path "$regkey\$($_.pschildname)" -Name NetbiosOptions -Value 2 -Verbose}Save this code to disableNetbios.ps1 file, copy it to your GPO directory, and run on clients via Computer Configuration -> Policies -> Windows Settings -> Scripts -> Startup- > PowerShell Scripts.
Then open a command prompt and run the following command to check that NetBIOS is disabled for your network adapters.
wmic nicconfig get caption,index,TcpipNetbiosOptionsHow to Disable NetBIOS Over TCP/IP in Intune?
My solution consists of 2 PowerShell scrips, both to be used with Microsoft Intune.
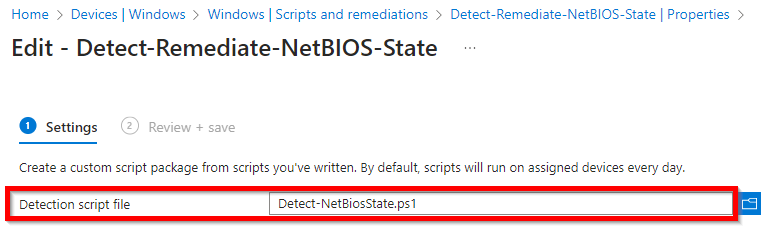
Detect-NetBiosState.ps1
#Detection Script
$Path = "HKLM:\SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces\tcpip*"
$Name = "NetbiosOptions"
$Type = "DWORD"
$Value = 2
Try {
$Registry = Get-ItemProperty -Path $Path -Name $Name -ErrorAction Stop | Select-Object -ExpandProperty $Name
$Counter = 0
Foreach ($Entry in $Registry )
{
If ($Entry -eq $Value)
{
$Counter+=0
}
else
{
$Counter+=1
}
}
if($Counter -eq 0)
{
Write-Output "OK"
Exit 0
}
else
{
Write-Warning "Not OK"
exit 1
}
}
Catch {
Write-Warning "Not OK"
Exit 1
}This script detects whether NetBIOS is currently disabled or not on the active network adapter. If NetBIOS is NOT disabled, the script will exit with error 1 instructing Microsoft Intune to run the remediation script.
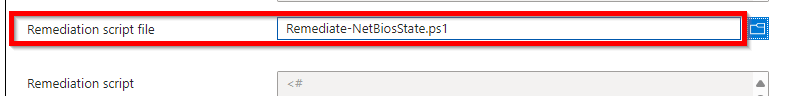
Remediate-NetBiosState.ps1
$Path = "HKLM:\SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces\tcpip*"
$Name = "NetbiosOptions"
$Type = "DWORD"
$Value = 2
Set-ItemProperty -Path $Path -Name $Name -Type $Type -Value $Value -ErrorAction SilentlyContinueThis script detects whether NetBIOS is currently disabled or not on the active network adapter. If NetBIOS is NOT disabled, the script will attempt to disable it.
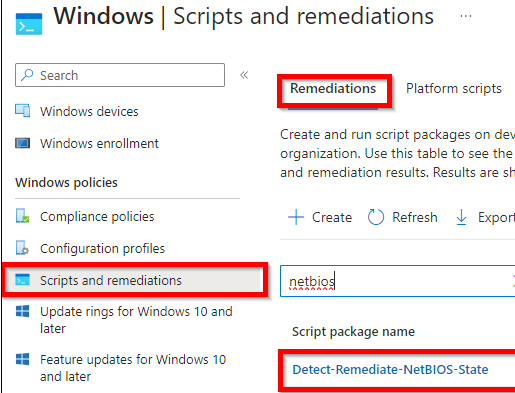
Put the 2 scripts to use in Microsoft Intune with the Remediations options as shown below: