
You may have heard about OS Credential Dumping during a penetration test or in the news, and now you may want to learn how to protect yourself from it.
What is OS Credential Dumping?
OS Credential Dumping is a technique used by attackers to extract authentication credentials from operating systems. The credentials may include:
- Plaintext passwords
- Password hashes
- Kerberos tickets
- Other authentication tokens stored in memory or on disk
This technique is commonly used during post-exploitation phases of a cyberattack to escalate privileges, maintain persistence, or facilitate lateral movement within a network.
How Does OS Credential Dumping Work?
Operating systems, especially Windows, store credentials in various locations for authentication purposes. Attackers target these locations using specialized tools or scripts to extract sensitive information.
Common Sources of Credentials in Windows:
LSASS Process:
- The Local Security Authority Subsystem Service (LSASS) process in Windows stores credentials in memory for active sessions.
- Tools like Mimikatz and ProcDump can extract these credentials.
SAM (Security Account Manager) Database:
- Located at
C:\Windows\System32\config\SAM, it stores hashed passwords of local user accounts. - Requires SYSTEM-level access.
- Often paired with the SYSTEM file to decrypt stored hashes.
Cached Domain Credentials:
- Windows caches by default las 10 credentials locally used for offline logins.
- These hashes can be dumped and cracked offline.
How can I defend against these attacks?
1. System Hardening
a. Enable LSASS Protection
- On Windows, enable LSASS protection to prevent unauthorized access to its memory:
- Modify the registry key:
HKLM\SYSTEM\CurrentControlSet\Control\Lsa
Add a DWORD value named RunAsPPL and set it to 1.
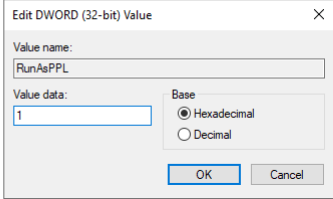
- Reboot the system.
b. Enable Credential Guard
- Use Windows Defender Credential Guard to isolate secrets in a virtualized environment, making it harder for attackers to access them.
c. Disable Cached Credentials
- Limit or disable the caching of domain credentials:
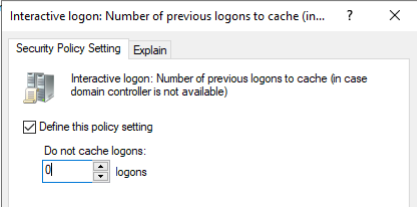
- Use Group Policy:
Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options
Set Interactive logon: Number of previous logons to cache to 0for servers when they have a continuous connection to the DC, and 1for workstations that need offline logins.
d. Regularly Patch Systems
- Apply security updates for operating systems and applications to close vulnerabilities attackers may exploit.
2. Restrict Access and Privileges
a. Implement Least Privilege
- Restrict administrative privileges to only those who absolutely need them. Avoid using admin accounts for routine tasks.
b. Limit Remote Access
- Disable or restrict access to remote management tools like RDP unless necessary.
- Use multifactor authentication (MFA) for remote access.
c. Secure Service Accounts
- Use Group Managed Service Accounts (gMSA) for automated account management.
- Regularly rotate passwords for service accounts.
- Add admin users to “Protected Users” group.