In this article, we will discuss how to secure our Active Directory. Before spending a lot of money on an expensive vulnerability assessment, you may want to take a look at Ping Castle!
It’s free to use if you don’t intend to make money from it, and it’s simple to use, so let’s take a look at it.
What it does?
PingCastle is a tool that quickly assesses the security of Active Directory by generating detailed reports. These reports provide scores across four key areas, explain any detected anomalies, and offer recommended solutions.
How to use it?
After downloading and unzipping it on a domain machine, you’ll find the following files in the folder.
Run the PingCastle.exe application, and you’ll see the following options displayed in a command-line interface.
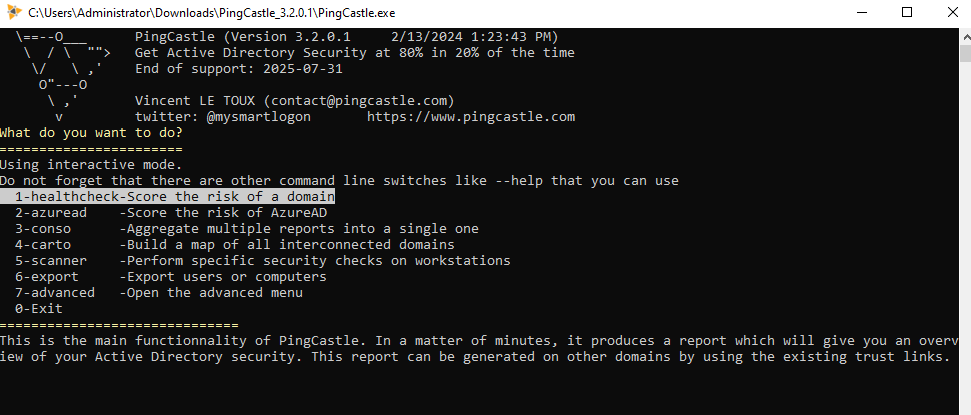
As you can see, there are several useful options. For this part, we’ll audit our Active Directory domain, but you also have the option to scan your AzureAD domain or a specific workstation. In another article, I’ll cover a different tool for the AzureAD scan. So here we’ll chose the first option.
You can specify the domain or server you want, but by default, it selects the domain of the machine. Simply press Enter to choose the default option. (This domain is part of my AD lab, and I’ll write another article on how to create a vulnerable AD for training purposes.)
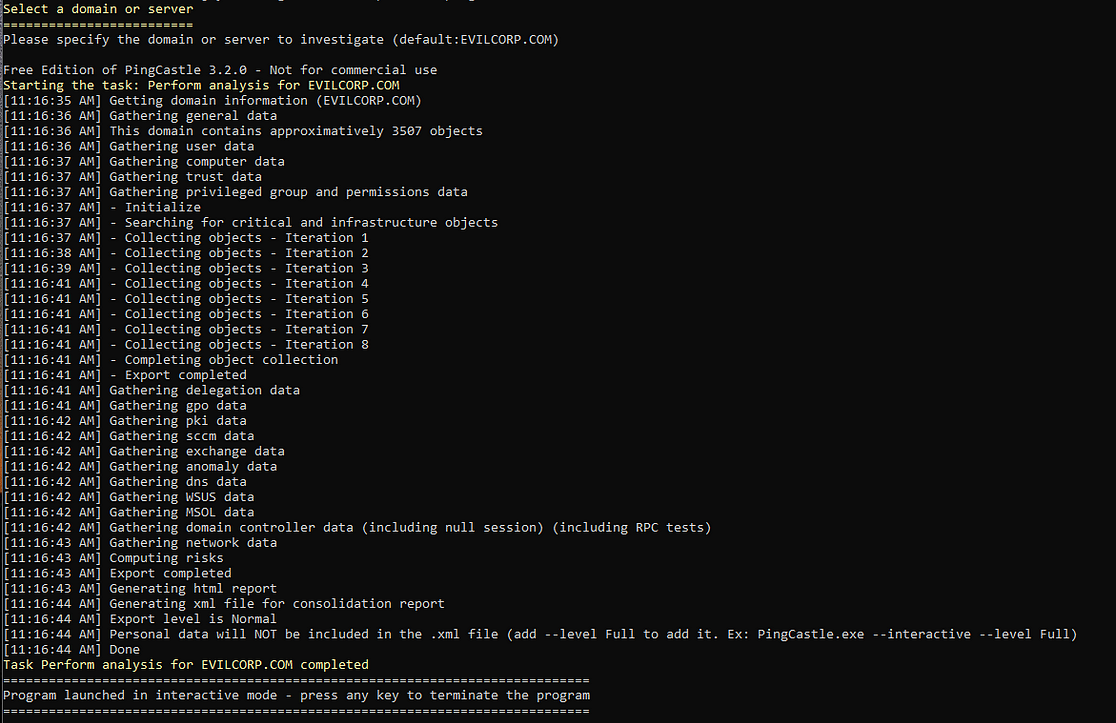
It will then start gathering information and running checks for the report. Once finished, it creates two files — a HTML and an XML file — in the application’s folder.
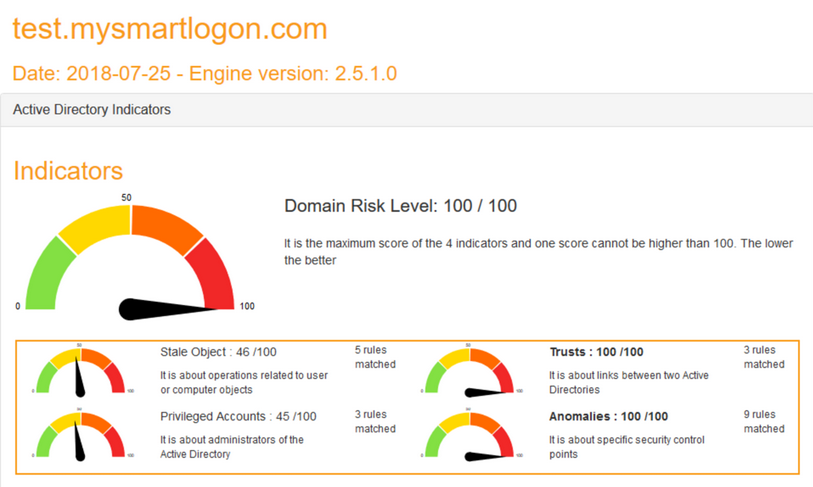
When we open the files, we can see the scores for the different areas. A score of 0 is excellent, while 100 is very poor.
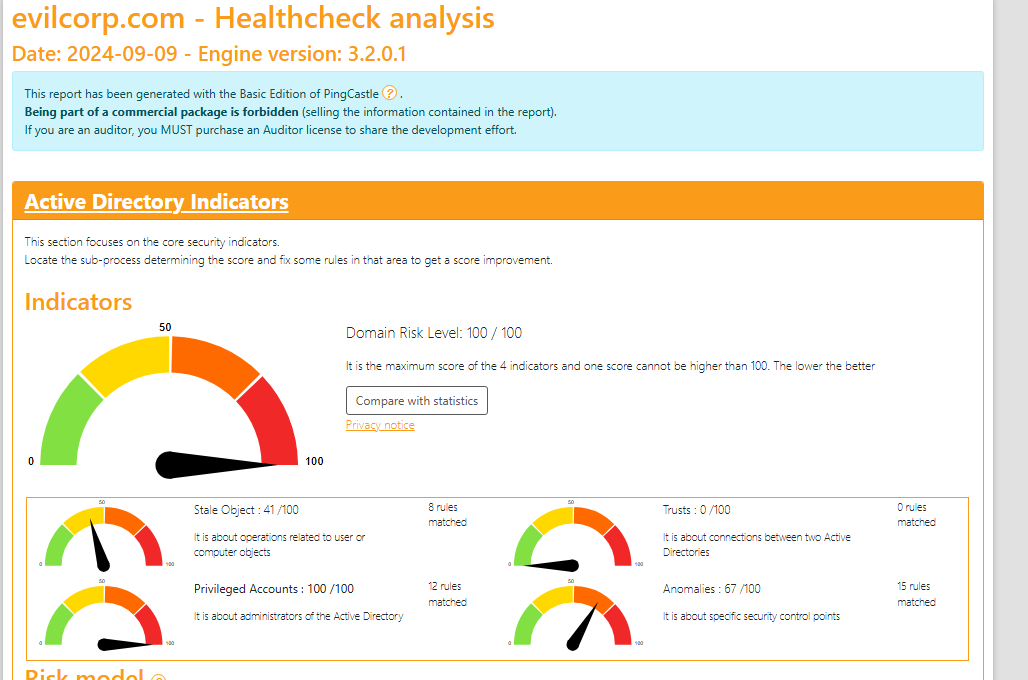
By going through each section, we can see a detailed list of the security checks we didn’t pass and which ones are more critical than others.
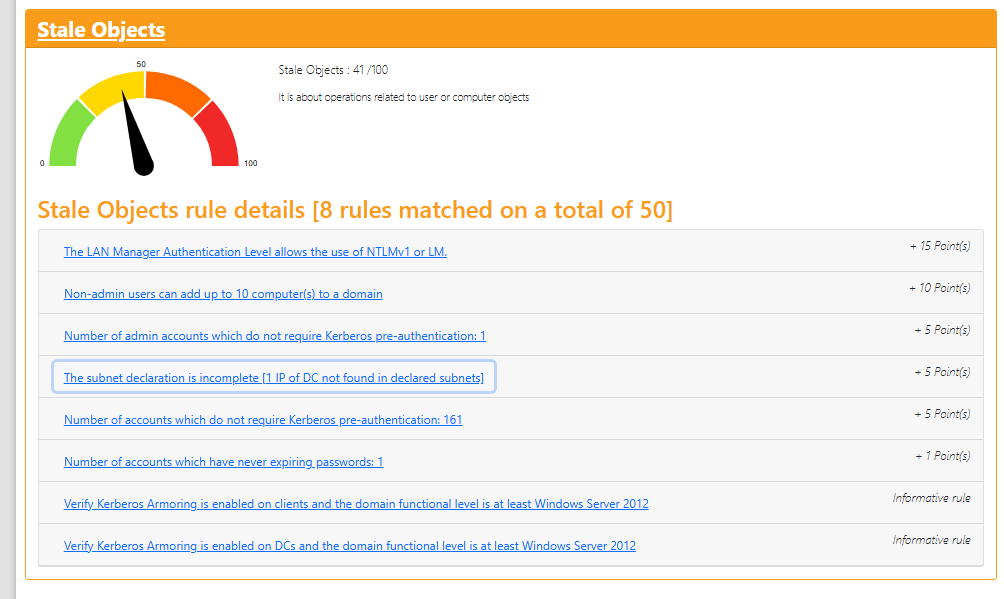
Clicking on each matched rule provides information about the issue, how to resolve it, and some useful links.
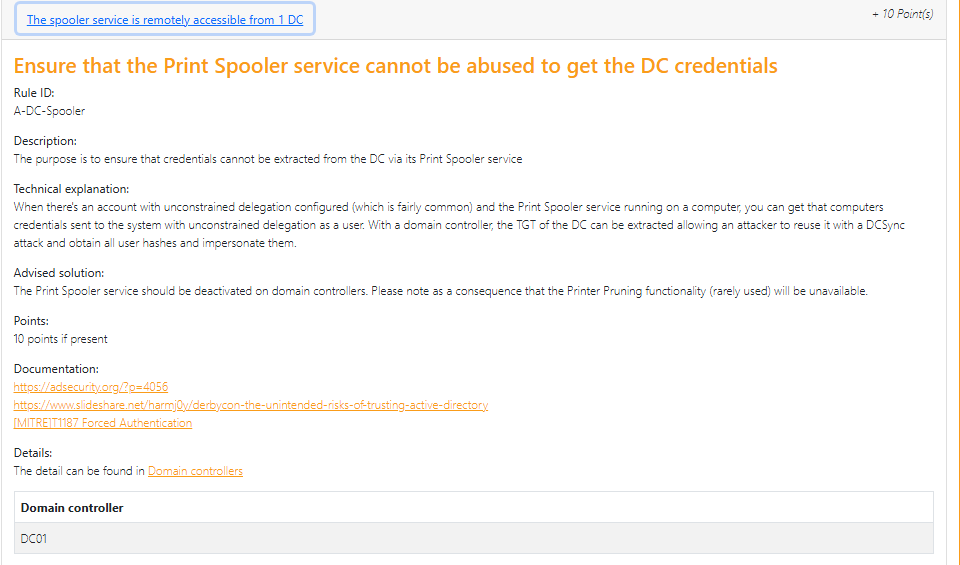
Before investing in an expensive security audit, use this application to address all the issues it identifies and aim to bring those scores down to 0. After that, you can consider a security audit.
Remember that each finding in the report should be carefully reviewed and added to a task list for our remedial action plan. It’s essential to understand each finding from a business standpoint, including the related risks, threats, and vulnerabilities. This understanding aids in evaluating how threats could exploit configurations, guiding both current and future strategies.