What is the KRBTGT account?
The user account: KRBTGT is an account that is automatically created when promoting the first domain controller of the domain (DC).
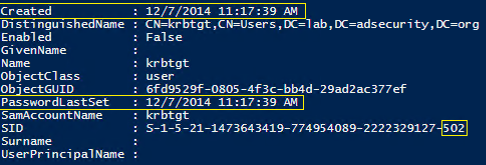
This account is located in the Active Directory container: Users.
The account description is as follows: “Key Distribution Center Service Account.”
The purpose of this account is to authenticate Kerberos tickets using the Key Distribution Center (KDC) service.
Why change the KRBTGT account password?
There are attackers who attempt to obtain the NTLM hash of the KRBTGT account, enabling them to generate Kerberos tickets and gain access rights to the entire AD environment.
How often is it recommended to change the KRBTGT account password?
The recommendation is to change the KRBTGT account password twice and every 180 days.
It is recommended to change the password twice because the KRBTGT account remembers the last two passwords when using Kerberos.
What is the danger of changing the KRBTGT password?
Changing the KRBTGT password once is not a problem, the issue arises when changing it twice without a sufficient time interval between the first and the second change.
The scenario is as follows:
- We change the KRBTGT password for the first time.
- The new KRBTGT password is replicated across all DCs.
- The new KRBTGT password will be used for all new tickets.
- Old tickets generated by the old KRBTGT password continue to work because the password history is set to “2,” meaning the last two passwords are valid.
- Both the new and old KRBTGT passwords remain valid.
- Once the old Kerberos tickets expire, they must be renewed using the new KRBTGT password.
If there hasn’t been enough time between the first and second password change, some Kerberos tickets will stop working.
To avoid problems, we can follow these steps:
1- Verify replication (*), change the KRBTGT password for the first time, force replication.
2- Wait, for example, 2 weeks.
3- Verify replication (*), change the KRBTGT password for the second time, force replication.
4- Wait for 180 days.
5- Return to the first point.
- If replication is not correct, we do not change the KRBTGT password anymore.
It’s not really necessary to wait for such a long time (2 weeks) between the first password change and the second. We could wait 24 hours, but this way we ensure that there won’t be any issues.
Microsoft comments on the need to change the password twice and the interval that should elapse between the first and second change:
Important:
“You should perform this operation twice. When resetting the Key Distribution Center Service Account password twice, a 10 hour waiting period is required between resets. 10 hours are the default Maximum lifetime for user ticket and Maximum lifetime for service ticket policy settings, hence in a case where the Maximum lifetime period has been altered, the minimum waiting period between resets should be greater than the configured value.”
Note:
The password history value for the krbtgt account is 2, meaning it includes the 2 most recent passwords. By resetting the password twice you effectively clear any old passwords from the history, so there is no way another DC will replicate with this DC by using an old password.
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/forest-recovery-guide/ad-forest-recovery-reset-the-krbtgt-password
How to view the date of the last password change for the KRBTGT account?
Via PowerShell, it can be done like this:
Get-ADUser "krbtgt" -Property Created, PasswordLastSet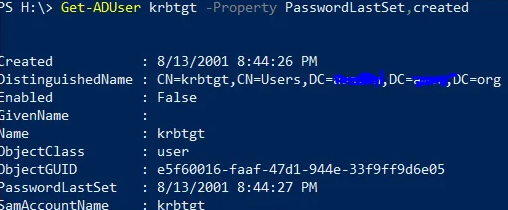
How to change the KRBTGT password in an automated manner?
Via PowerShell, it can be done like this, dynamically generating a complex random password:
Set-ADAccountPassword -Identity (Get-ADUser krbtgt).DistinguishedName -Reset -NewPassword (ConvertTo-SecureString -AsPlainText -Force (New-Guid).Guid)